NoPass™ is a multi-factor authentication add-on for remote users. In addition to the username and password, NoPass performs two additional factors of authentication - something you have and something you are. This utilises smartphones and does not require the purchase of additional hardware authentication devices for each user. Nor does it use SMS, which can also be costly.
No more passwords!
Password-based security has become a liability in recent times due to sophisticated phishing attacks and challenges faced by users to create and manage numerous passwords. The centralised storage of millions of user credentials including passwords within the cloud or a website server provides a single point of attack for hackers, which can greatly increase the cost of a single data breach. Online attacks like Man-in-the-Middle (MitM) and Man-in-the-Browser (MitB) can pose a substantial threat to online authentication by secretly modifying the communication between the user and server.
NoPass™ is very simple, very secure
Along with very strong security, the user does not need to enter a password. The NoPass™ server and application in the phone takes care of all of the bi-directional handshakings, requiring only that the user compare two images (a picture and a 3-digit number), then swipe or touch the approve button, and they are connected.
Decentralised Authentication
Centralised passwords lead to mass breaches and credential reuse. The continued use of centralised passwords alongside 'passwordless experiences' gives companies a false sense of security while they remain vulnerable to credential stuffing attacks. When companies store user credentials in a centralised repository, they create a huge target for hackers and invite credential reuse. The centralised credential store is a hackers' favourite target. It represents a single point of failure, there's a high risk of breach, it's susceptible to credential re-use and it's expensive to secure and maintain. In all these ways, centralised passwords are lacking. | 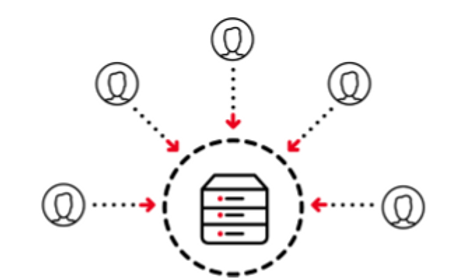 |
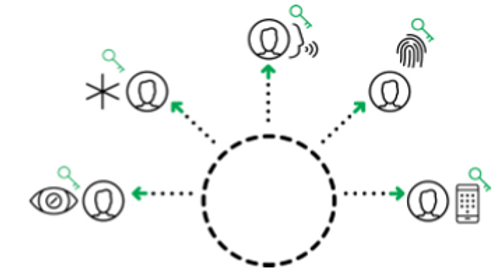
Decentralised authentication enables true passwordless security. Organisations are replacing the use of centralised passwords with decentralised authentication. Rather than storing millions of passwords in a single repository, user credentials are decentralised and stored safely on their personal devices. This approach removes the hackers' primary target and renders credential stuffing attacks infeasible. Decentralised credentials are: - stored safely on personal devices
- true passwordless architecture
- stop mass breaches, fraud and phishing
- resistant to credential re-use
- low cost to secure and maintain
|  |
